Silicon IP Cores
SHA-256
256-bit SHA Secure Hash Crypto Engine
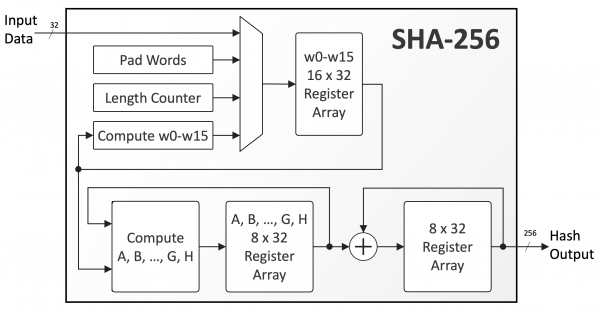
The SHA-256 encryption IP core is a fully compliant implementation of the Message Digest Algorithm SHA-256. It computes a 256-bit message digest for messages of up to (264 – 1) bits.
Developed for easy reuse in ASIC and FPGA applications, the SHA-256 is available optimized for several technologies with competitive utilization and performance characteristics. Support for AMBA bus interfaces and integration with an external DMA are available as options.
The SHA-256 can be used in various applications for ensuring data integrity, and authenticity. Some examples are on-chip communication, electronic fund transfers, digital signatures, password storage, blockchain technology and data backup.
The core has been verified through extensive synthesis, place and route and simulation runs. It has also been production-proven in several ASIC and FPGAs designs.
Support
The core as delivered is warranted against defects for ninety days from purchase. Thirty days of phone and email technical support are included, starting with the first interaction. Additional maintenance and support options are available.
Deliverables
The core is available in RTL (VHDL or Verilog) source code, or as a targeted FPGA netlist. Its deliverable package includes the following:
- Sophisticated HDL self-checking testbench
- C Model & test vector generator
- Sample simulation and synthesis scripts
- User documentation
The SHA-256 can be mapped to any ASIC technology or FPGA device (provided sufficient silicon resources are available). The following are sample ASIC pre-layout results reported from synthesis with a silicon vendor design kit under typical conditions, with all core I/Os assumed to be routed on-chip. The provided figures do not represent the higher speed or smaller area for the core. Please contact CAST to get characterization data for your target configuration and technology.
| Technology | Logic Resources |
Memory Resources |
Fmax (MHz) |
Throughput (Gbps) |
|---|---|---|---|---|
| TSMC 40nm | 29,985 eq. gates | - | 800 | 6.302 |
| TSMC 28nm HPM | 14,674 eq. gates | - | 1,000 | 3.938 |
| TSMC 16nm | 17,963 eq. gates | - | 1,400 | 11.028 |
The SHA-256 can be mapped to any ASIC technology or FPGA device (provided sufficient silicon resources are available). The following are sample Altera® results with all core I/Os assumed to be routed on-chip. The provided figures do not represent the higher speed or smaller area for the core. Please contact CAST to get characterization data for your target configuration and technology.
| Technology | Logic Resources |
Memory Resources |
Freq. (MHz) |
Throughput (Mbps) |
|---|---|---|---|---|
| MAX 10 (-7) | 2,068 LEs | - | 125 | 895 |
| Arria 10 GX (-1) | 893 ALMs | - | 125 | 895 |
| Stratix V (-3) | 901 ALMs | - | 200 | 1,575 |
| Stratix V (-1) | 900 ALMs | - | 225 | 1,772 |
The SHA-256 can be mapped to any ASIC technology or FPGA device (provided sufficient silicon resources are available). The following are sample AMD results with all core I/Os assumed to be routed on-chip. The provided figures do not represent the higher speed or smaller area for the core. Please contact CAST to get characterization data for your target configuration and technology.
| Technology | Logic Resources |
Memory Resources |
Freq. (MHz) |
Throughput (Mbps) |
|---|---|---|---|---|
| Kintex UltraScale (-1) | 1,265 LUT | - | 350 | 2.757 |
| Virtex-7 (-3) | 1,183 LUT | - | 350 | 2.757 |
| Kintex UltraScale+ (-1) | 1,268 LUT | - | 400 | 3.151 |
| Virtex UltraScale (-3) | 1,224 LUT | - | 400 | 3.151 |
| Versal (-2) | 1,193 LUT | - | 400 | 3.151 |
Engineered by Ocean Logic.
Features List
- NIST-Validated SHA-256 implementation compliant to FIPS 180-4
- Input length up to (264 – 1) bits
- High throughput:
- 65 clock cycles per 512-bit input block
- Over 10Gbps on modern ASIC technologies
- Throughput scaling with multiple clock instances.
- Small Silicon footprint: 15k-20k Gates
- Easy integration & implementation
- Fully synchronous, uses only the rising clock-edge, single-clock domain, no false or multicycle timing paths, scan-ready, LINT-clean, reusable design
- Simple input and output interfaces optionally bridged to AMBA™ interfaces or integrated with a DMA engine.
- Available in VHDL or Verilog source code format, or as a targeted FPGA netlist
- Complete deliverables include test benches, C model, and test vector generator
- Multiple times production-proven in ASIC and FPGA designs
Resources
Wikipedia: SHA Hash Functions